OAuth 1.0 and OAuth 2.0 in .NET Core
In today’s interconnected digital world, ensuring secure access to your web applications is paramount. One of the most trusted and widely used methods for user authentication and authorization is OAuth. In this blog post, we’ll delve into the world of OAuth 1.0 and OAuth 2.0, and explore how to seamlessly integrate them into your .NET Core projects. By the end of this guide, you’ll have a solid understanding of both mechanisms and be equipped to implement them with confidence.
What is OAuth?
OAuth is an authorization framework that allows a third-party application to access resources on behalf of a user. The user authorizes the third-party application to access their resources by providing their credentials, such as their username and password. The third-party application then uses these credentials to obtain an access token from the resource owner. The access token is used to access the user’s resources. It is a popular choice for authentication in .NET Core projects because it is secure, flexible, and easy to implement.
There are two primary versions of OAuth in use today: OAuth 1.0 and OAuth 2.0. While both serve similar purposes, they have distinct differences in terms of architecture and security mechanisms.
OAuth 1.0:
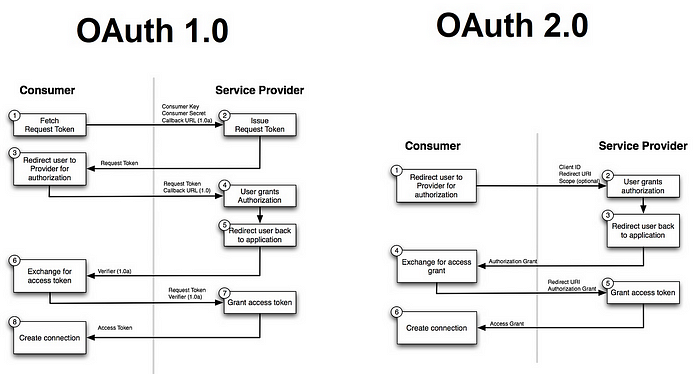
OAuth 1.0 is the earlier version of the protocol and is based on a more complex process involving cryptographic signatures. This version includes three main roles:
- User: The individual seeking to grant access to their resources.
- Consumer: The third-party application that wants access to the user’s resources.
- Service Provider: The server hosts the user’s resources.
The OAuth 1.0 flow involves multiple steps, including request token acquisition, user authorization, and access token retrieval. While it provides a high level of security, the complexity of handling cryptographic signatures and nonces can make its implementation challenging, It means- It uses signatures and timestamps to authenticate requests, which can make it difficult to implement.
How to implement OAuth in .NET Core?
There are a number of ways to implement OAuth in .NET Core projects. One way is to use the Microsoft.AspNetCore.Authentication.OAuth NuGet package. This package provides a number of OAuth providers, such as Google, Facebook, and Twitter.
To use the Microsoft.AspNetCore.Authentication.OAuth NuGet package, you need to add it to your project's dependencies. You can do this by running the following command in the Package Manager Console:
Install-Package Microsoft.AspNetCore.Authentication.OAuth
Once the package is installed, you need to configure the OAuth provider that you want to use. You can do this by adding the following code to your project’s Startup.cs file:
services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = OAuthDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = OAuthDefaults.ChallengeScheme;
options.AddProvider(new GoogleOAuthProvider());
});
This code configures the OAuthDefaults.AuthenticationScheme and OAuthDefaults.ChallengeScheme to be used for authentication and challenge, respectively. It also adds GoogleOAuthProvider to the list of providers.
To obtain an access token, you can use the AuthenticateAsync() method of the IAuthenticationManager interface. The following code shows how to obtain an access token from the Google OAuth provider:
var authenticationManager = HttpContext.Features.Get<IAuthenticationManager>();
var result = await authenticationManager.AuthenticateAsync("Google");
if (result.Succeeded)
{
var accessToken =
result.Principal.Identity.Claims.FirstOrDefault(c => c.Type == "access_token").Value;
}
This code uses the AuthenticateAsync() method to authenticate the user with the Google OAuth provider. If the authentication is successful, the access token is returned.
Real-world implementations of OAuth
There are many real-world implementations of OAuth. Some of the most popular ones include:
- Google OAuth: This is used by many Google services, such as Gmail and Google Drive.
- Facebook OAuth: This is used by many Facebook applications.
- Twitter OAuth: This is used by many Twitter applications.
- GitHub OAuth: This is used by many GitHub applications.
OAuth 2.0: Simplicity and Flexibility
OAuth 2.0 was introduced to simplify the protocol and make it more developer-friendly. It focuses on access token issuance, with the roles of the user, client (formerly known as a consumer), and authorization server (replacing the service provider) being retained. OAuth 2.0 offers several grant types, including the Authorization Code Grant, Implicit Grant, Client Credentials Grant, and Resource Owner Password Credentials Grant.
For the purpose of this guide, we’ll primarily focus on the Authorization Code Grant, which is widely used for web applications.
Implementing OAuth 2.0 in .NET Core: Step by Step
Here’s a step-by-step guide to implementing OAuth 2.0 in a .NET Core project using the Authorization Code Grant:
Step 1: Create a New .NET Core Web Application
Start by creating a new .NET Core web application using your preferred development environment.
Step 2: Set Up the OAuth Provider
Choose an OAuth provider. For example, you can use IdentityServer4, a popular open-source framework for implementing OAuth 2.0 in .NET Core applications.
Install the IdentityServer4 NuGet package:
Install-Package IdentityServer
Step 3: Configure IdentityServer
In your Startup.cs file, configure IdentityServer by adding the necessary services and middleware. Define the API resources, client applications, and their respective scopes.
public void ConfigureServices(IServiceCollection services)
{
// IdentityServer4 Configuration
services.AddIdentityServer()
.AddInMemoryApiResources(Config.GetApiResources())
.AddInMemoryClients(Config.GetClients())
.AddDeveloperSigningCredential();
// Other services...
}
Step 4: Create Configuration Classes
Create classes to define API resources and client applications in the Config class:
public static class Config
{
public static IEnumerable<ApiResource> GetApiResources()
{
return new List<ApiResource>
{
new ApiResource("api", "My API")
};
}
public static IEnumerable<Client> GetClients()
{
return new List<Client>
{
new Client
{
ClientId = "client_id",
ClientSecrets = { new Secret("client_secret".Sha256()) },
AllowedGrantTypes = GrantTypes.Code,
RedirectUris = { "https://localhost:5001/oauth-demo" },
AllowedScopes = { "openid", "profile", "api" }
}
};
}
}
Step 5: Add Authentication Middleware
To learn about the middleware concepts — refer here:
In the Configure method of your Startup.cs file, add the IdentityServer4 authentication middleware.
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
// Other middleware...
app.UseIdentityServer();
// Other configuration...
}
Step 6: Create a Controller to Handle Authentication
Create a controller that handles the authentication process, including the redirection to the IdentityServer4 authorization endpoint.
public class AccountController : Controller
{
private readonly SignInManager<IdentityUser> _signInManager;
private readonly IHttpClientFactory _httpClientFactory;
public AccountController(SignInManager<IdentityUser> signInManager, IHttpClientFactory httpClientFactory)
{
_signInManager = signInManager;
_httpClientFactory = httpClientFactory;
}
[HttpGet]
public IActionResult Login(string returnUrl)
{
var props = new AuthenticationProperties
{
RedirectUri = returnUrl,
Items = { { "hello", "oauth2" } }
};
return Challenge(props, "oauth2");
}
// Other actions...
}
Advantages of OAuth 2.0
- Simplified Workflow: OAuth 2.0 reduces the complexity of the authentication process compared to OAuth 1.0, making it more approachable for developers.
- Scalability: OAuth 2.0’s token-based approach allows for easier scalability and integration with various platforms and devices.
- Flexible Grant Types: OAuth 2.0 provides multiple grant types to cater to different scenarios, such as web applications, mobile apps, and machine-to-machine communication.
- Widespread Adoption: OAuth 2.0 has gained widespread adoption, making it easier to find libraries, tools, and resources for implementation.
Consider a scenario where you’re building a social media integration for your .NET Core application. By implementing OAuth 2.0, you can seamlessly allow users to authenticate using their social media accounts and access their profile information.
OAuth 1.0 and OAuth 2.0 are powerful tools for enabling secure and seamless authentication and authorization in your .NET Core projects. OAuth 2.0’s simplified workflow, flexibility, and widespread adoption make it an ideal choice for modern web applications. By following the steps outlined in this guide and exploring real-world implementations, you’re well on your way to becoming an OAuth integration expert. So, go ahead and empower your applications with the strength of OAuth mechanisms, ensuring your users’ data remains secure while delivering a smooth user experience.