Post-Quantum Readiness: Why Blockchain Roadmaps Need to Act Now
Most blockchain roadmaps fixate on the next six-month sprint—scalability tweaks, token launches, UX polish. Yet the White House’s 2022 quantum-security memorandum and the UK NCSC’s roadmap both circle 2035 as the hard deadline for abandoning today’s vulnerable public-key crypto. Wait for a one-million-qubit breakthrough, and you’ll be scrambling instead of shipping. That’s why post-quantum risk deserves a first-class spot on your roadmap today—just look at ecosystem pilots like Project 11 for proof.
Why protocol and application teams should care now
Upgrading a live blockchain is never a weekend Git merge. Bitcoin’s Taproot soft fork took almost four years, from the 2017 proposal to its November 2021 activation. Ethereum’s shift to proof-of-stake began with the Beacon Chain in December 2020 and finalized on September 15, 2022, according to Ethereum.org. These timelines reveal three truths:
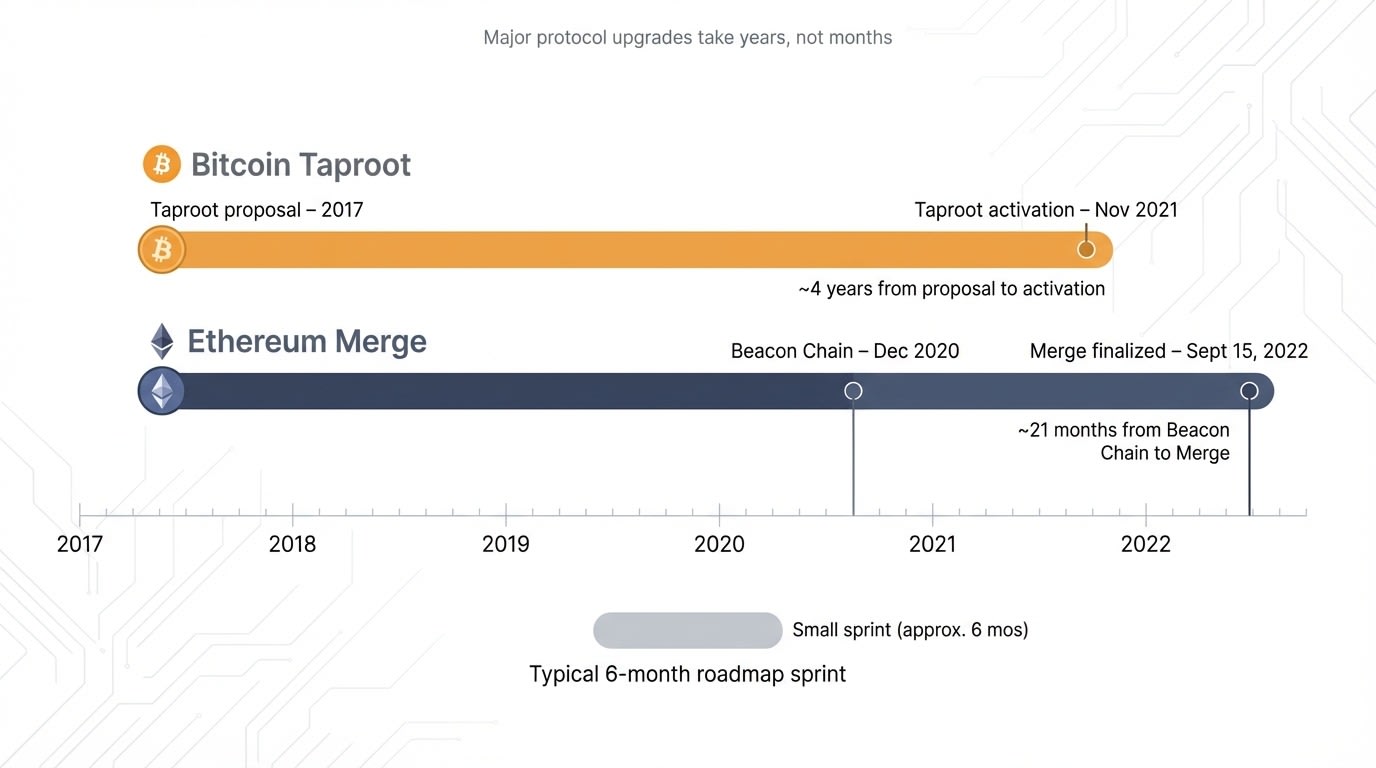 Real-world protocol upgrades like Bitcoin Taproot and Ethereum’s Merge take years, not months.
Real-world protocol upgrades like Bitcoin Taproot and Ethereum’s Merge take years, not months.
- Core cryptography sits deep inside consensus rules, wallets, and smart contracts.
- Every change needs social agreement, testnets, and sometimes a hard fork or flag-day release.
- Rushing a migration risks chain splits, lost funds, and reputation damage.
Put simply, we need several years, not months, to design, test, socialize, and deploy post-quantum protection. Wait for the first one-million-qubit headline, and you’ll patch under pressure instead of shipping with confidence.
Three questions to ask about quantum readiness
What cryptographic assumptions does your chain rely on?
Most blockchains still use ECDSA signatures and SHA-256 or Keccak hashes. Map exactly where these primitives appear in validation rules, wallet libraries, and smart-contract pre-compiles, because every exposed public key becomes a future target. More than 25 percent of all bitcoin reveal their public keys on-chain, according to a Coindesk analysis, proving how easy it is to overlook this surface area.
Which assets or modules would fail first if Q-Day arrived tomorrow?
Start with the obvious risk items: reused pay-to-pubkey addresses, multisig treasuries that publish every member key, and any contract that time-locks funds behind the same key for months. Shor-class hardware could drain these in minutes, so give them top priority in your threat model.
What migration levers do you control, both technical and social?
Post-quantum address formats and validation rules only ship when governance moves quickly and wallets auto-migrate users. Bitcoin’s Taproot process shows that even a soft fork took about four years from proposal to activation, according to Coindesk. Build CLI scripts, wallet prompts, and multisig rotation helpers now, so your community doesn’t write emergency patches on Q-Day.
Answering these three questions turns a distant concern into a concrete, sprint-level roadmap item and gives you a head start on the inevitable upgrade cycle.
Building quantum into your technical roadmap
Think of post-quantum work as grease in an engine you’re already tuning, not a separate rebuild. We fold the effort into three live streams:
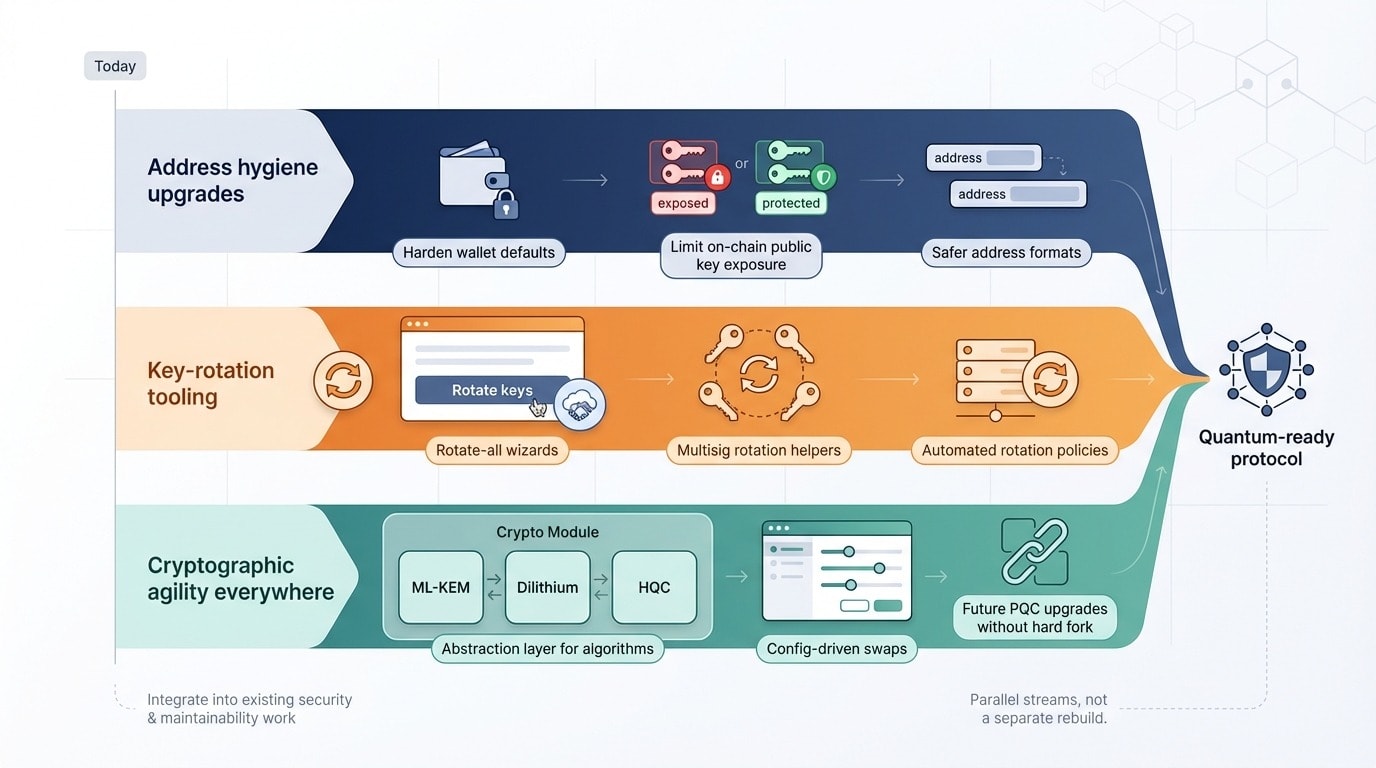 Post-quantum work fits into three ongoing streams: address hygiene upgrades, key-rotation tooling, and cryptographic agility.
Post-quantum work fits into three ongoing streams: address hygiene upgrades, key-rotation tooling, and cryptographic agility.
- Address hygiene upgrades. Harden defaults so wallets reveal fewer public keys. Bitcoin research shows that about 25 percent of outputs already expose their keys on-chain, according to NIST.
- Key-rotation tooling. Chrome and Cloudflare’s 2019 CECPQ2 test showed that large post-quantum keys can travel through today’s TLS with single-digit-millisecond overhead, as reported by Cloudflare. Shipping rotate-all wizards for users and multisig contracts offers similar breathing room.
- Cryptographic agility everywhere. A 2025 NIST draft paper on crypto agility (CSWP-39) calls for modules that “swap algorithms without interrupting a running system.” Build that swap layer now so a future ML-KEM-to-HQC change is a config tweak, not a hard fork.
Framing these items as routine security and maintainability tasks keeps momentum high today while preparing the chain for the first real quantum headline.
The role of external research and metrics
None of us need PhDs in lattice math, but we do need a dashboard. A Capgemini report states that 70 percent of large organizations are evaluating post-quantum cryptography, yet only 15 percent qualify as “quantum-safe champions” with mature governance. A Quantum-Safe Financial Forum survey adds that 86 percent of firms admit they’re still unprepared. These figures keep the conversation grounded, not abstract.
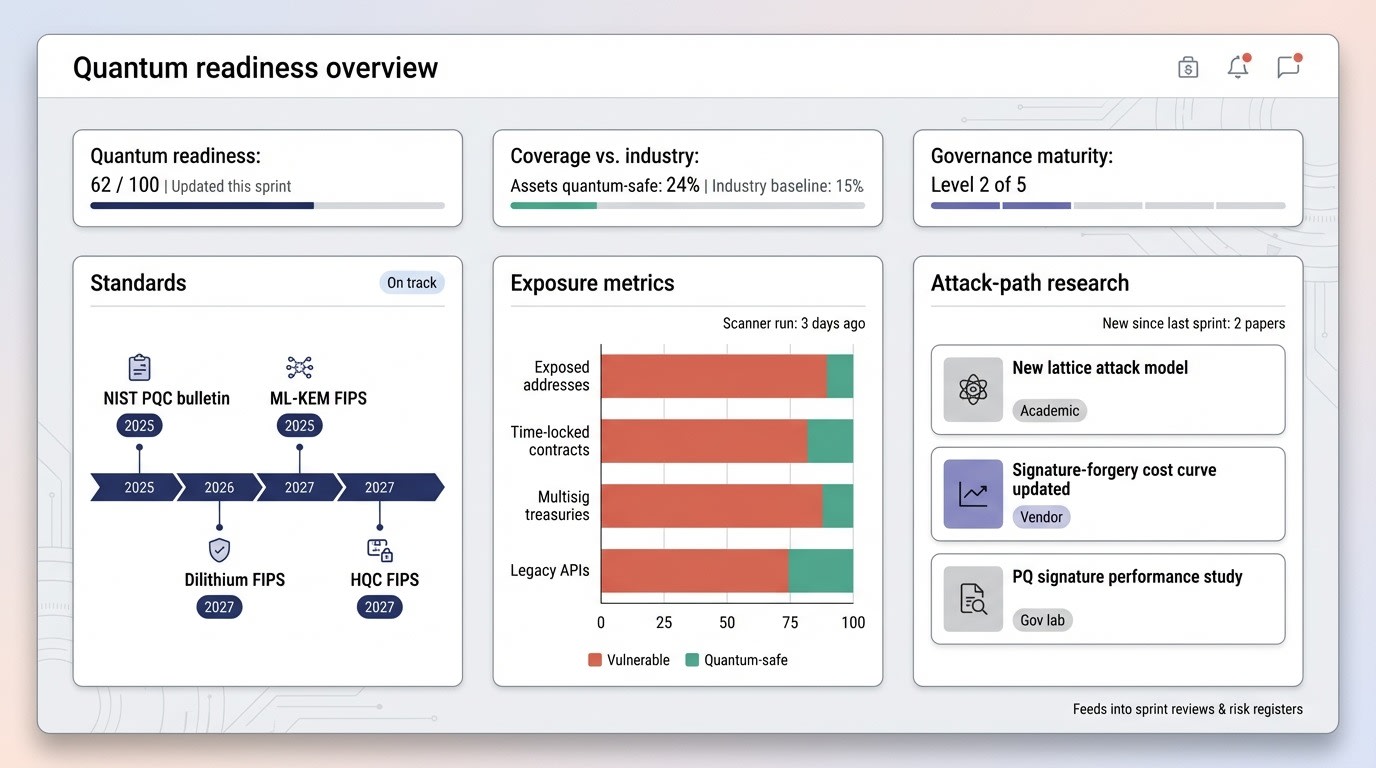 A quantum-risk dashboard helps blockchain teams track standards, exposure metrics, and new attack-path research in one view.
A quantum-risk dashboard helps blockchain teams track standards, exposure metrics, and new attack-path research in one view.
To stay ahead, track three external signal streams:
- Standards: Follow NIST’s rolling PQC bulletins; the agency expects final FIPS publications for ML-KEM, Dilithium, and HQC by 2027.
- Exposure metrics: Tools such as Project 11’s open-source scanner count how many addresses, contracts, or APIs in your stack still publish vulnerable keys. Project 11 also estimates that more than $50 billion has already been poured into quantum-computer R&D, so its Bitcoin Risq List dashboard turns that macro threat into a line-by-line ledger of your own exposure.
- Attack-path research: Subscribe to papers from PQShield, ANSSI, and university labs that model specific breakpoints, such as signature-forgery cost curves.
Use these sources in sprint reviews, risk registers, and roadmap OKRs. The aim is not to read every paper; instead, ensure you always have a current, quantified view of your ecosystem’s exposure.
Communicating with your community
Technical merit alone never ships an upgrade; social legitimacy does. During Ethereum’s 2022 Merge, core developers published no fewer than six public testnet blog posts (#TestingTheMerge) and hosted open Discord war rooms that anyone could join, according to blog.ethereum.org updates. That steady cadence of updates turned a risky shift to proof-of-stake into a celebrated milestone.
Why copy that playbook?
- Governance risk is real. An analysis of 429 top-volume tokens found that 75 percent carry governance red flags, from hidden owners to single-sig treasuries, according to Cointelegraph.
- Trust gaps block adoption. A multi-country PwC survey showed that lack of user trust ranks in the top three barriers to blockchain rollouts, even as 84 percent of executives pilot the tech.
When we brief you on quantum-safety plans, we:
- Explain the threat in plain English, without doom or jargon.
- Publish what is known, what is uncertain, and the next checkpoints.
- Flag the trade-offs early (key-size bloat, migration cost).
This openness builds the political capital we will need when a future hard-fork vote appears on-chain.
Conclusion
Staying ahead of quantum threats demands foresight, technical agility, and transparent governance. By integrating post-quantum safeguards into today’s roadmap—and communicating progress clearly—blockchain teams can ship with confidence long before the first one-million-qubit headline hits.